This year, I had the privilege to attend the 2020 Medical Device Security 101 Conference held in New Orleans. I flew all the way from Zurich, where I am a research student at ETH Zurich. I came to the conference to learn more about current trends in medical device security and share the insights I gained with the medical device security community.
The conference, which was focused on helping attendees learn and network, gave me the opportunity to meet key representatives from the medical device security industry. The evening before the conference began, I attended a dinner sponsored by MedCrypt for speakers and organizers. Additional sponsors for the event included the University of Minnesota, H-ISAC, NetLib Security, Synopsys, and Virta Labs.

The first day of the conference started with a welcome speech by Prof. Kevin Fu, founder and chief scientist of the Archimedes Center for Medical Device Security, which organized the conference. Professor Fu’s mission is to improve medical device security through research and education and his pioneering research has served as a benchmark for the medical device industry. During his introduction, Professor Fu highlighted the biggest challenge facing cybersecurity—the human factor. “It is not exclusively about technology anymore.”
How Cybersecurity Impacts Physician and Patient Relationships
Following Professor’s Fu’s welcome, Dr. David Slotwiner, chief of the cardiology division at New York Presbyterian Queens, discussed his thoughts on the human role in cybersecurity from both a patient and physician perspective. In a look at the pros and cons of remote monitoring allowed by medical devices, Dr. Slotwiner highlighted the patient benefits and outlined the necessary consent process and its implications.
He noted that even if pacemakers and implantable cardioverter defibrillators (ICD) enable fewer hospitalizations, increased survival rates, and greater monitoring efficiency, in urgent situations patients aren’t able to have an opinion regarding the privacy of their data. Although physicians review consent with their patients, these circumstances can lead to miscommunication.
The difficulties start when patients need to regularly visit the hospital to update their devices; are they willing to do that? Do they have a choice? And most importantly, what about recalls? What is the procedure for both patients and physicians when that happens? Physicians must be able to interpret risks and vulnerabilities introduced by their patients’ medical devices so that they can address these questions when they arise.
Dr. Slotwiner provides a solution to this problem: education. Physicians must learn about the cybersecurity landscape—the existing infrastructure, ongoing risks, and patient expectations. If physicians are properly informed, they’ll be able to properly set expectations for patients.
However, it’s not just physicians who need to get educated on medical device security. Patients should understand how their health could be affected if a vulnerability in their medical device is exploited, how to mitigate those risks, and how to manage specific threats on their own. Overall, the relative benefit of therapy must overcome the threat risk, and patients need to understand the risks versus rewards to make informed decisions about their treatment.

To close up the morning sessions, Dr. Suzanne Schwartz, deputy director of the FDA’s Office of Strategic Partnerships & Technology Innovation (OST), provided us with relevant regulatory updates followed with a Q&A session. Under the most important updates, she informed attendees about the publication of the Cybersecurity Premarket Guidance, which is currently published as a draft. The FDA is planning to release the final version of the document as soon as 2021, including in the guidance outcomes from several workshops and sessions that will take place during this coming year.
Dr. Schwartz also talked about how the FDA is collaborating with international regulators from around the globe through the International Medical Device Regulators Forum (IMDRF) to achieve a consistent global standardization regarding medical device cybersecurity. This would facilitate policy processes for manufacturers, which have supply chains spread across multiple countries and continents.
In addition, the FDA will be organizing threat modelling bootcamps for medical device manufacturers, which will be led by Adam Shostack, author of Threat Modeling: Designing for Security (Wiley, 2014) and co-author of The New School of Information Security (Addison-Wesley, 2008). Dr. Schwartz said the FDA will be developing a playbook to help the industry overcome cybersecurity challenges, the two biggest of which are legacy device management in healthcare facilities and patient communication. She agrees with Dr. Slotwiner on the importance of improving communication to prevent patients from refusing to use medical devices, despite their immense benefits.
“There is definitely a lot going on,” Dr. Schwartz said, “and there is definitely a need for alignment and support from all stakeholders and regulators in the healthcare sector.”

Practical Approach to Defend Medical Environments
Many healthcare organizations struggle in their efforts to develop and maintain a practical approach to securing their medical devices. Jay Radcliffe (CISSP), director of product security testing and research at Thermo Fisher Scientific, shared a plan healthcare providers can use to tackle medical device security that focuses on optimizing efforts and costs while getting an understanding of what security measures need to be taken.
From a technical perspective, Radcliffe suggests first obtaining a device inventory to get an overview of all the assets within the organization and which ones need to be defended. For that, Radcliffe suggests avoiding active scanning, since it could be problematic. Instead, he recommends using the tool Rumble (https://www.rumble.run/), which employs new techniques for probing the network specifically to find inventory. Here, MAC (Media Access Control) addresses can be very useful for classifying devices and clustering. (A MAC address is a unique identifier assigned to a network interface controller for use as a network address in communications within a network segment.) Radcliffe also advises segmenting the network structurally into small subnetworks using data flows and network maps as a reference to boost performance and improve security.
Radcliffe also stressed the importance of security education and the need for physicians to better understand the technical aspects of the devices they use and prescribe. He discussed how collaborating with vendors could improve security.
Year in Review: Regulations and Standards
 Diving back into policy, Charles Farlow (CISSP), president of Farlow Systems Consulting, and Michelle Jump, MedSec’s global regulatory advisor for medical device security, provided an update on regulations and standards. Charles went over the cybersecurity regulatory timeline, commenting again on the FDA’s premarket cybersecurity guidance draft. Farlow also provided an overview of the regulation environments in Canada, Australia, and France, along with the IMDRF. From the Canadian premarket requirements, the device specific risk management process proposed is adopted from the ISO 14971, where safety and security risk management processes are conducted in parallel. Farlow emphasized that it’s critical for manufacturers to follow risk control activity.
Diving back into policy, Charles Farlow (CISSP), president of Farlow Systems Consulting, and Michelle Jump, MedSec’s global regulatory advisor for medical device security, provided an update on regulations and standards. Charles went over the cybersecurity regulatory timeline, commenting again on the FDA’s premarket cybersecurity guidance draft. Farlow also provided an overview of the regulation environments in Canada, Australia, and France, along with the IMDRF. From the Canadian premarket requirements, the device specific risk management process proposed is adopted from the ISO 14971, where safety and security risk management processes are conducted in parallel. Farlow emphasized that it’s critical for manufacturers to follow risk control activity.
Farlow shared a table created by Australia’s Therapeutic Goods Administration (TGA) that summarizes the standards recognized as suitable to meet regulatory requirements for medical device cybersecurity, alongside the essential principles represented. The TGA also provides valuable graphs regarding cybersecurity risks broken down into White Hat and Black Hat. It’s definitely worth the time to examine these documents.
Farlow recommended using the Medical Device Coordination Group’s guidance since it globalizes the relevant essential requirements of the European Union’s Medical Device Regulation (MDR) and In Vitro Diagnostic Medical Devices (IVDR) directive and references the IMDRF Principles and Practices for Medical Device Cybersecurity.
Jump gave an update of the following standards: AAMI TIR 97, AAMI SW 96, IEC 60601-4-5, ISO/IEC TR 80001-5-1 and ISO/IEC 81001-1. Of all the standards, only AAMI TIR 97, which outlines the principles for medical device security postmarket risk management for device manufacturers, is not under development. The conference gave a complimentary copy of the standard to each attendee who came to the event, which we could reference during the session.
The main reason to focus on postmarket security management is that risks emerge differently, which is why this standard appends a further process on the postmarket risk management decision diagram. Jump also brought up an important point about how strong security measurements could also lead to safety consequences and vice versa. This trade-off needs to be taken into consideration while applying security mitigations.
From the other standards in progress, Jump highlighted the lifecycle framework on addressing safety and the effectiveness of health software and health IT systems found in the ISO/IEC 81001-1, which she considers very relevant.

Cybersecurity in the Wearable Medical Devices: Unique Challenges
Wearable medical devices can reduce hospital readmissions and assist in monitoring health conditions, but they also present security challenges around confidentiality, integrity, availability, and authenticity. On top of these known challenges, we should be aware of the unique security challenges machine learning introduces, said Sagar Patel, cybersecurity lead at Battelle.
In his talk, Patel shone a light on open problems that need to be addressed including the lack of training data, biases in machine learning datasets, and the optimization of energy efficiency while using cryptographic algorithms. Patel did provide potential solutions, encouraging attendees to be aware of low-hanging fruit and use standard authentication algorithms and authorization schemas when designing medical devices.
In the last session of the day, HDR Vice President and Engineering Principal Tim Koch led an inspirational talk focused on securing buildings, such as hospitals, rather than devices.
Koch said he started to understand the critical relationship between cybersecurity and operational systems (OS) while working with the University of Nebraska to build an operational technology incident simulator.
“There really is a risk and impact, so this is why we started to work on a framework of best practices for healthcare cyber-physical protection,” Koch said. He has been working with other experts to consider different use cases that need to be covered and identify appropriate requirements. At the close of the session, Koch invited attendees to assist him in understanding the problem and exchanging ideas, encouraging an inclusive and collaborative approach to building safer healthcare facilities.
To close the first day of the conference, attendees enjoyed a gala dinner on the New Orleans Riverboat with gorgeous views of the Mississippi River. The evening was accompanied by a fantastic Jazz band that provided a lively background for a fun night of networking among guests and speakers.

Threat Modeling Lessons from Star Wars
Networking opportunities were plentiful at the conference, starting up again on the second day with a breakfast where we had the opportunity to talk to most of the conference speakers. I joined Adam Shostack’s table and he gave us some insights into the FDA’s threat modelling bootcamp coming up this year.
The first bootcamp will include 20 experts who will frame the structure for the second bootcamp session. In the latter, about 60 professionals from the medical device industry will be able to attend, and they will all work together on developing a playbook. Shostack said this step toward using threat modelling more consistently will help the industry better secure its products and facilities.
Privacy and Cybersecurity in Neuromodulation Systems
After the breakfast, Dr. Erika Petersen, who directs the section of functional and restorative neurosurgery at the University of Arkansas Medical Center, gave a presentation on privacy and cybersecurity in neuromodulation systems from a physician’s perspective. In her work, Dr. Petersen implants neurological medical devices using a broad set of technological tools. She often tries to educate her residents at the hospitals to be more aware of technologies they are using and the involved risks. She encourages residents to consider, for example, “What would happen if a device breaks in an emergency surgery?” Neurological surgeries depend on millimeter accuracy to be successful, which is why it’s vital to have medical equipment that meets extreme standards in reliability.
Dr. Petersen also cited the importance of teaching data privacy awareness. In the hospital, residents wear smartwatches and use phones that may gather data that shouldn’t be disclosed. In Dr. Petersen’s opinion, HIPAA compliance should also consider the real implications of these consumer technologies. Private companies collect data from these Internet of Things (IoT) devices and can use that data for their research, whereas academics from the health sector need difficult-to-acquire approval to employ data collected from pacemakers. This imbalance, said Dr. Petersen, slows down healthcare improvements.
An exciting panel discussion on the importance of regulations and standards for software transparency followed Dr. Petersen’s presentation. Matt McMahon, acting product and solution security officer for Siemens Healthineers’ EMEA region; Audra Hatch, product security specialist at Thermo Fisher Scientific; Michael Dittamo, information security risk manager at New York Presbyterian Hospital; and Michelle Jump were on the podium ready to answer questions from the audience about software bills of materials (SBOM). The idea behind this strategy is to collect and share more vulnerability information from the software supply chain to establish standardized processes that could be particularly valuable for risk management.
SBOM’s strength is that it brings together both medical device manufacturers and healthcare delivery organizations to achieve a greater industry impact. During the discussion, panelists encouraged the audience to join this initiative and help during phase II of SBOM development, which will address challenges regarding recall and disposition.

Debunking Hyperbole in Healthcare Security from a Data-Driven Perspective
To wrap up the morning, MedCrypt Chief Security Strategist Axel Wirth shared insights garnered from years analyzing an increasing rise in healthcare security breaches.
Email phishing is still the most common attack vector, Wirth said, explaining that malicious attacks now target data rather than actual devices. He added that the increase of known breaches over the past years are mainly a result of regulations that force organizations to disclose vulnerabilities. Wirth encouraged manufacturers to not worry too much about the rise in breaches, but rather prioritize patching.
Organizations often use the Common Vulnerability Scoring System (CVSS) to evaluate where to place resources on security mitigation, but proof shows that no strong correlation between CVSS and patching frequency exists. Wirth urges caution and careful application of CVSS. But above all, he said, “security has to become proactive, since we will not succeed with a reactive approach.”

The Battle for Medical Device Security Continues
Author and security consultant Adam Shostack kept the audience awake after lunch with a thrilling presentation about threat modelling using analogies from Star Wars. Threat modelling, Shostack said, is a healthy practice for engineering secure systems in a structured way.
The procedure is based on four simple questions that need to be answered:
- What are we working on?
- What can go wrong?
- What are we going to do about it?
- Did we do a good job?
If the company can answer these questions, Shostack said, they’re on the right track.
To answer the second question, Shostack suggests reviewing security threats with STRIDE: spoofing, tampering, repudiation, information disclosure, denial of service, and elevation of privileges. Shostack drew on stories from Star Wars to explain what these threats exactly mean. In order to understand the remediation procedure for these threats, properties are paired with their respective mitigation approaches. The properties originate from the classic CIA triad—confidentiality, integrity, and availability—but also include authentication, non-repudiation, and authorization.
Shostack concluded his talk by presenting ten traps on how threat modelling can go wrong or give an erroneous perception of security. However, if used correctly, Shostack said, “threat modelling can be the most effective way to drive security through your product, service, or system.”
Weaving Privacy Into Security Risk Assessments
If a physician forgets to turn on a feature in an implanted device and their patient dies on the way home, could the physician face a lawsuit? Yes, they most definitely could, said Boston Scientific R&D System Engineer Grace Wiechman, who spoke on data privacy in technology.
Wiechman has been studying how to better assess the implied risks in medical devices from a privacy point of view. She claims that collecting even a little information from medical devices could result in disclosure of data. But it’s not just about the amount of data these devices collect. In the hypothetical example above, the small amount of data collected from the deceased patient’s implanted device would be enough evidence to involve the negligent physician in a lawsuit.
Wiechman advises planning for future business cases and doing your research to perform better privacy impact analyses. She also recommends keeping medical devices simple so that they collect only data that’s necessary and adopting a privacy by design approach when developing medical devices. Designing a device with the most restrictive regulation from the beginning, she said, can save a lot of headaches.
Security Architecture Analysis
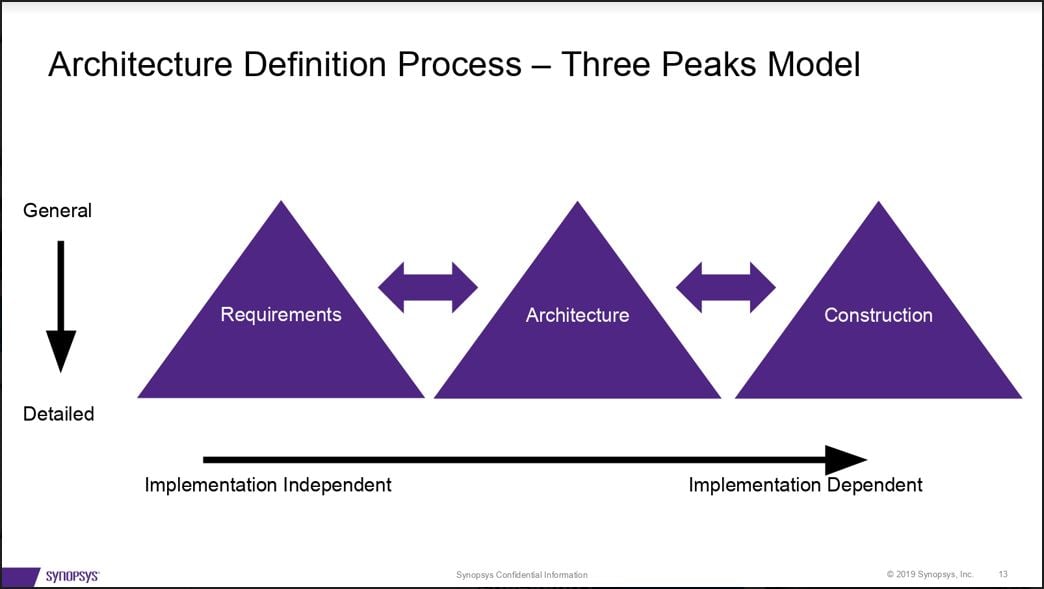
Security risk assessment is essential during the entire system development process to balance costs with security. In his session on security architecture basics, Synopsys Principal Consultant Dan Lyon explained how medical device manufacturers can reduce costs by identifying security design flaws in the context of risk relevance.
Lyon advised security architects to set general requirements first before designing architecture and constructing their systems, then iterate the process in more detail.
In order to calculate the likelihood of a risk occurrence in a risk assessment, Lyon suggests using qualitative approaches first and then semi-quantitative methods, if necessary. He supports the idea of starting simple and then determining if a more detailed evaluation is required. “Start with the forest,” he said, “not with the trees.”
Lost in Practical Translation: Patient Safety to Cybersecurity Risk
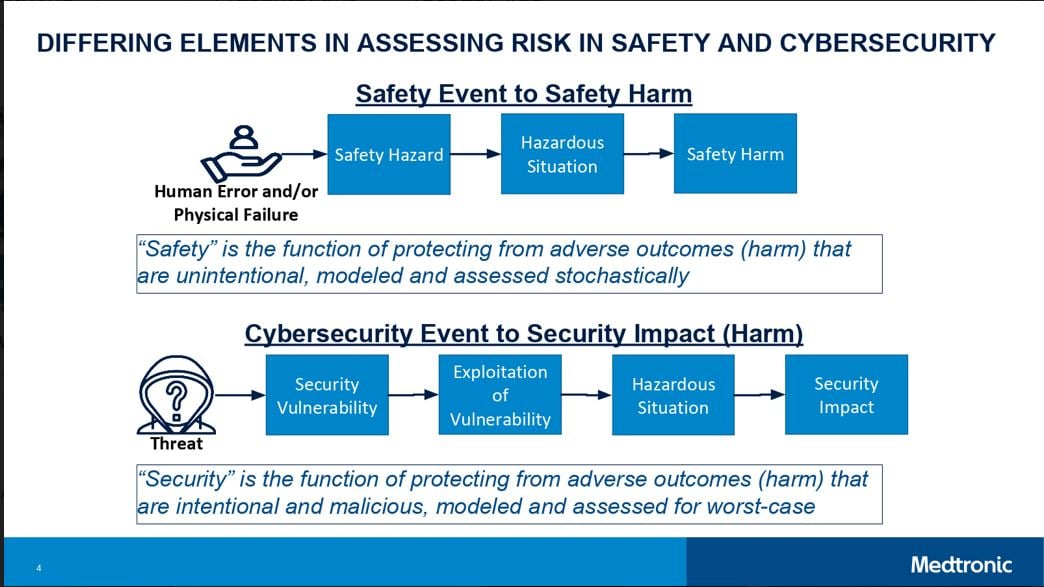
Medtronic’s Dr. Alex Kent wrapped up the second day of talks explaining why it’s so difficult to assess patient safety and security risk using a combined approach.
Dr. Kent presented a new translation that connects the two parallel approaches for assessing risk in using medical devices. One approach focuses on patient safety and the other focuses on potential cybersecurity impact. A new obstacle for risk assessment is the translation from cybersecurity to safety, e.g. estimating to what extent security threats have potential safety impact.
“How do we objectively assess a potential patient safety harm event given a security vulnerability, and how is a potential harm event assessed given a more traditional safety hazard?” asked Dr. Kent. This question, he said, is a current challenge for the medical device industry.
Dr. Kent highlighted the need for more data to better understand the landscape and provide an improved risk assessment. For example, he said, the common vulnerability scoring system (CVSS) can be used to achieve more consistency and objectivity in assessing vulnerabilities and can help us to comprehend the future. Dr. Kent’s team, together with FDA and other partners, are working on enhancing the risk management processes, which he considers non-trivial for premarket and postmarket practices. He invited the audience to exchange ideas and work together to improve the process.
.jpg?width=2560&name=My%20Post%20(3).jpg)
About the Author
 Sofia Martinez Gomez has a background in robotics control and systems with a focus on medical devices, which she studied at ETH Zurich and NTU Singapore. For the last two years, she has been building on her passion for robotics with cybersecurity courses, which have provided her with a multidisciplinary technical knowledge. In combination with her studies, Sofia works as a cyber security consultant at Deloitte AG in Switzerland. Sofia is currently writing her thesis in collaboration with Roche Diagnostics, where she is developing a quantitative methodology to estimate the probability of zero-day incidents in medical devices. The goal of her research is to provide an industry framework that can be implemented during risk management processes.
Sofia Martinez Gomez has a background in robotics control and systems with a focus on medical devices, which she studied at ETH Zurich and NTU Singapore. For the last two years, she has been building on her passion for robotics with cybersecurity courses, which have provided her with a multidisciplinary technical knowledge. In combination with her studies, Sofia works as a cyber security consultant at Deloitte AG in Switzerland. Sofia is currently writing her thesis in collaboration with Roche Diagnostics, where she is developing a quantitative methodology to estimate the probability of zero-day incidents in medical devices. The goal of her research is to provide an industry framework that can be implemented during risk management processes.

